Home / Blog
|
Protect Your WebSite from Being Hacked
Hacking is a regular occurrence worldwide over the internet. e-Mail,
Social Networking and other online accounts are at risk from being hacked
into if care is not taken to keep secure information safe.
Hacking is regularly performed by automated scripts written to scour the
Internet in an attempt to exploit known website security issues in software.
Here are our top 07 tips to help keep you and your site safe online.
1) Keep software up to date
It may seem obvious, but ensuring you keep all software up to date is
vital in keeping your site secure. This applies to both the server operating
system and any software you may be running on your website such as a CMS
or forum. When website security holes are found in software,
hackers are quick to attempt to abuse them.
If you are using third-party software
on your website such as a CMS or forum, you should ensure
you are quick to apply any security patches. Most vendors have a mailing
list or RSS feed detailing any website security issues.
WordPress, Umbraco and many other CMSes notify you of available system
updates when you log in.
2) SQL injection
SQL injection attacks are when an attacker uses a web form field or URL
parameter to gain access to or manipulate your database. When you use
standard Transact SQL it is easy to unknowingly insert rogue code into
your query that could be used to change tables, get information and delete
data.
You can easily prevent this by always using parameterised queries, most
web languages have this feature and it is easy to implement.
"SELECT * FROM table WHERE column = '" + parameter + "';"
If an attacker changed the URL parameter to pass in ' or '1'='1 this will
cause the query to look like this:
"SELECT * FROM table WHERE column = '' OR '1'='1';"
Since '1' is equal to '1' this will allow the attacker to add an additional
query to the end of the SQL statement which will also be executed.
3) XSS
Cross site scripting is when an attacker tries to pass in JavaScript or other scripting code into a web form to attempt to run malicious code for visitors of your site. When creating a form always ensure you check the data being submitted and encode or strip out any HTML.
4) Error messages
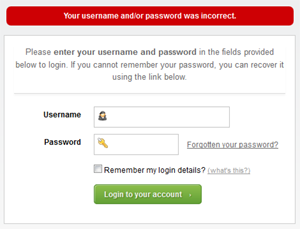
| Be careful with how much information you give away in
your error messages. For example if you have a login form on your website you should think about the language you use to communicate failure when attempting logins. You should use generic messages like “Incorrect username or password” as not to specify when a user got half of the query right. If an attacker tries a brute force attack to get a username and password and the error message gives away when one of the fields are correct then the attacker knows he has one of the fields and can concentrate on the other field. |
 |
5) Passwords
Everyone knows they should use complex passwords, but that doesn’t mean
they always do. It is crucial to use strong passwords to your server and
website admin area, but equally also important to insist on good password
practices for your users to protect the security of their accounts.
As much as users may not like it, enforcing password requirements such
as a minimum of around eight characters, including an uppercase letter
and number will help to protect their information in the long run.
Passwords should always be stored as encrypted values, preferably using
a one way hashing algorithm such as SHA. Using this method means when
you are authenticating users you are only ever comparing encrypted values.
For extra website security it is a good idea to salt the passwords, using
a new salt per password.
In the event of someone hacking in and stealing your passwords, using
hashed passwords could help damage limitation, as decrypting them is not
possible. The best someone can do is a dictionary attack or brute force
attack, essentially guessing every combination until it finds a match.
When using salted passwords the process of cracking a large number of
passwords is even slower as every guess has to be hashed separately for
every salt + password which is computationally very expensive.
6) File uploads
Allowing users to upload files to your website can be a big website security
risk, even if it’s simply to change their avatar. The risk is that any
file uploaded however innocent it may look, could contain a script that
when executed on your server completely opens up your website.
If you have a file upload form then you need to treat all files with great
suspicion. If you are allowing users to upload images, you cannot rely
on the file extension or the mime type to verify that the file is an image
as these can easily be faked. Even opening the file and reading the header,
or using functions to check the image size are not full proof. Most images
formats allow storing a comment section which could contain PHP code that
could be executed by the server.
7) SSL
SSL is a protocol used to provide security over the Internet. It is a good idea to use a security certificate whenever you are passing personal information between the website and web server or database. Attackers could sniff for this information and if the communication medium is not secure could capture it and use this information to gain access to user accounts and personal data.
If you have any question or need consultation, please do not hesitate to contact us at: support@yi.com.pk

